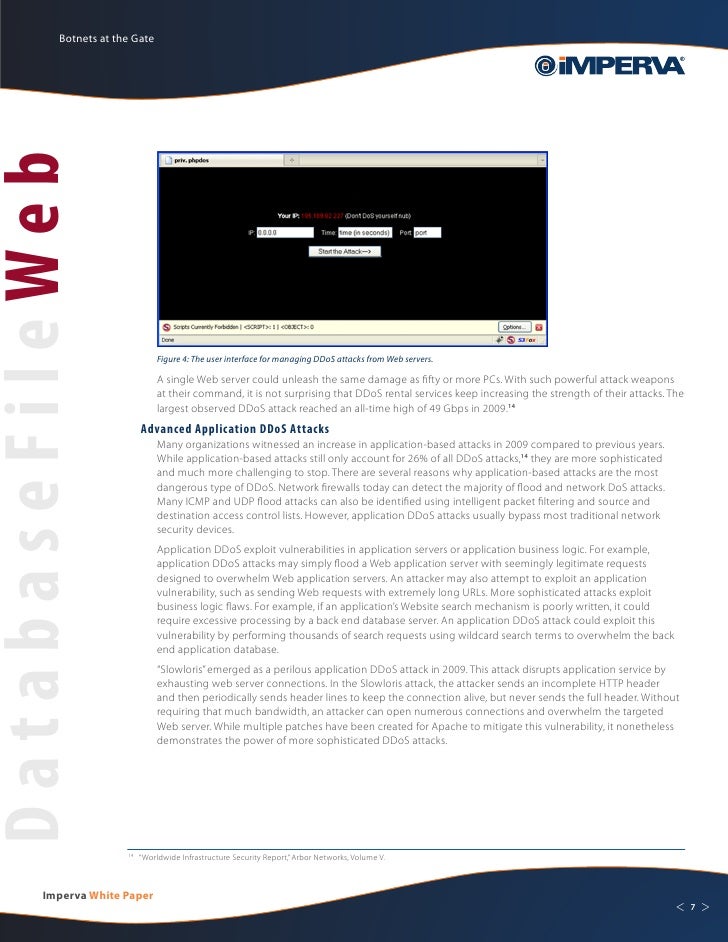
Blackenergy Ddos Bot
From the dark side comes an ominous new botnet called Darkness that researchers say is quite impressive and is targeting a wide variety of websites. In the last month, Darkness has become a very active DDoS network being controlled by several domains hosted in Russia. Darkness operators are boasting that it can take down larges sites with only 1,000 bots and for as little as $50 a day.
The first BlackEnergy samples researched by Arbor Networks in 2007 were of a web-distributed DDoS bot, used to target Russian sites while using Malaysian and.
Analysis, the botnet 'Destination Darkness Outlaw System'(D.D.O.S), aka 'Darkness' is said to have superior performance to BlackEnergy and Illusion botnets. 'Upon testing, it was observed that the throughput of the attack traffic directed simultaneously at multiple sites was quite impressive. As with BlackEnergy, 'Darkness' is easy to purchase, easy to deploy, and is very effective and efficient in what it does.' To refresh your memory, discovered that BlackEnergy botnet delivered a 1 - 2 punch to financial institutions. Cybercriminals had morphed the code into a more malicious software that stole banking passwords, deleted files to cover tracks and then launched DDoS attacks.
'The same botnet that's being used to steal money from banks is launching these denial-of-service attacks on them,' Joe Steward, a researcher at Secureworks,. There are many ads popping up in the malware ecosystem that promote Darkness. After translating one claim, Darkness offers the 'support of 3 controlling URLs at once. It is a long awaited feature and is very useful in case of a domain suspension or IP address change on the 'abuse hosting.' ' Additionally, an states:.
30 bots overwhelm an average site. Yes, just 30. 300 bots - a medium size site. 1000 bots - large site. 5000 - cluster with site, even when using anti-ddos, blocks, and other preventive measures.
15-20 thousand bots can theoretically bring down vkontakte.ru (Russian Facebook) Shadowserver agrees that Darkness can be configured with three domains to be used as Command and Control (C&C). Having three C&C allows attackers to 'backup in case of hosting takedown or domain suspension.' The Darkness botnet has attacked over 100 targets in the last month, including financial and e-commerce sites. Right now, the botnet is using these three domains for C&C: hellcomeback.ru, greatfull-tools.ru and greatfull.ru. The following ad appears on another: Good day, dear citizens of DL! For your attention high quality service DDos We have the best price and quality!
We take any project regardless of the subject matter of the target! Constant customers individual conditions!
The average price of service from $ 50 per day Depends on the complexity of the attacked site Methods of payments are accepted via WebMoney For people who are interested in the work on an ongoing basis is a separate proposal on which you will not regret it. After Darkness infects a system, the malware calls out to one of the C&C domains for commands. The server then responds to the bot with a base64 encoded set of instructions for the DDoS attack. Darkness can attack listed targets with DDoS traffic via HTTP, ICMP, or TCP/UDP. Shadowserver noted, 'It now appears that 'Darkness' is overtaking BlackEnergy as the DDoS bot of choice. There also appear to be no shortage of buyers looking to add 'Darkness' to their botnet arsenal.' The battle against botnet crime-ware is on ongoing one.
The FBI recently took down the mastermind behind the malicious 'Mega-D.' Authorities said 'he was the king of spam, a 23-year-old Russian controlling a network of infected computers generating 10 billion unwanted e-mails a day - a third of the global spam stream - until a Milwaukee FBI agent unplugged the operation,'.
Hopefully more security-minded hackers and researchers will join the forces of light to battle against the forces of Darkness. Top image credit.
Blackenergy Malware
From the dark side comes an ominous new botnet called Darkness that researchers say is quite impressive and is targeting a wide variety of websites. In the last month, Darkness has become a very active DDoS network being controlled by several domains hosted in Russia. Darkness operators are boasting that it can take down larges sites with only 1,000 bots and for as little as $50 a day. Analysis, the botnet 'Destination Darkness Outlaw System'(D.D.O.S), aka 'Darkness' is said to have superior performance to BlackEnergy and Illusion botnets. 'Upon testing, it was observed that the throughput of the attack traffic directed simultaneously at multiple sites was quite impressive.
As with BlackEnergy, 'Darkness' is easy to purchase, easy to deploy, and is very effective and efficient in what it does.' To refresh your memory, discovered that BlackEnergy botnet delivered a 1 - 2 punch to financial institutions. Cybercriminals had morphed the code into a more malicious software that stole banking passwords, deleted files to cover tracks and then launched DDoS attacks. 'The same botnet that's being used to steal money from banks is launching these denial-of-service attacks on them,' Joe Steward, a researcher at Secureworks,.
There are many ads popping up in the malware ecosystem that promote Darkness. After translating one claim, Darkness offers the 'support of 3 controlling URLs at once. It is a long awaited feature and is very useful in case of a domain suspension or IP address change on the 'abuse hosting.' ' Additionally, an states:. 30 bots overwhelm an average site.
Yes, just 30. 300 bots - a medium size site. 1000 bots - large site. 5000 - cluster with site, even when using anti-ddos, blocks, and other preventive measures. 15-20 thousand bots can theoretically bring down vkontakte.ru (Russian Facebook) Shadowserver agrees that Darkness can be configured with three domains to be used as Command and Control (C&C). Having three C&C allows attackers to 'backup in case of hosting takedown or domain suspension.'

The Darkness botnet has attacked over 100 targets in the last month, including financial and e-commerce sites. Right now, the botnet is using these three domains for C&C: hellcomeback.ru, greatfull-tools.ru and greatfull.ru.
The following ad appears on another: Good day, dear citizens of DL! For your attention high quality service DDos We have the best price and quality!
We take any project regardless of the subject matter of the target! Constant customers individual conditions! The average price of service from $ 50 per day Depends on the complexity of the attacked site Methods of payments are accepted via WebMoney For people who are interested in the work on an ongoing basis is a separate proposal on which you will not regret it. After Darkness infects a system, the malware calls out to one of the C&C domains for commands. The server then responds to the bot with a base64 encoded set of instructions for the DDoS attack.

Darkness can attack listed targets with DDoS traffic via HTTP, ICMP, or TCP/UDP. Shadowserver noted, 'It now appears that 'Darkness' is overtaking BlackEnergy as the DDoS bot of choice.
There also appear to be no shortage of buyers looking to add 'Darkness' to their botnet arsenal.' The battle against botnet crime-ware is on ongoing one. The FBI recently took down the mastermind behind the malicious 'Mega-D.' Authorities said 'he was the king of spam, a 23-year-old Russian controlling a network of infected computers generating 10 billion unwanted e-mails a day - a third of the global spam stream - until a Milwaukee FBI agent unplugged the operation,'. Hopefully more security-minded hackers and researchers will join the forces of light to battle against the forces of Darkness. Top image credit.